Discover how LHV reduced manual work and tripled true positive rate with customisable monitoring rules
Read the case studyTransaction monitoring refers to the monitoring of transfers, deposits and withdrawals, in real time or after they have been processed by a bank or financial institution. Transaction monitoring is an important part of a financial crime compliance programme: not only does it help to detect patterns of suspicious behaviour, it also provides a complete view of customers’ activity, including customer risk levels and predictions of future behaviour.
Just like in Philip K. Dick’s “The Minority Report” novel, transaction monitoring, among other things, uses predictive mechanisms to detect and prevent crime before it happens by uncovering “red flags” in the past transactions and analysing the patterns in customer data. Unlike in the dystopian universe, Salv incorporates multiple conditions to identify bad behaviour and minimise risks to your business. We utilise both rules-based and risk-based approaches in transaction monitoring, including comprehensive rules that cover all risks specific to each industry and individual business.
This blog aims to give you a better understanding of transaction monitoring rules: how you can create, change, and test transaction monitoring rules, relieve pressure on your compliance team, and take your transaction monitoring to the next level. With Salv, you can do all of this – and more.
Before we go any further, let’s cover the basics of transaction monitoring.
What is transaction monitoring?
Transaction monitoring helps organisations to recognise and understand patterns of criminal behaviour, stop suspicious payments, or analyse them post-payment. Different types of transaction monitoring are used to improve the accuracy and speed of the enhanced due diligence (EDD) process, detect and prevent fraud, and analyse transactional data to detect money laundering.
Types of transaction monitoring
- Real-time transaction monitoring allows you to detect crime when it happens, and block suspicious payments in real time. This type of transaction monitoring is particularly valuable in detecting and preventing fraud.
- Post-event transaction monitoring is used in less critical situations, where the payments don’t raise immediate alarm. In post-event transaction monitoring, completed payments are compared against money laundering typologies in order to uncover hidden patterns.
- Periodic transaction monitoring is used to check historical customer data to better understand patterns and irregularities in the customer behaviour. Salv generates data aggregations for weekly or monthly transactional behaviour samples.
Who benefits from transaction monitoring
Transaction monitoring is a mandatory process for any regulated organisation. In addition to the obvious, such as banks and financial institutions, the list includes money services businesses (MSBs), payment service providers (PSPs), virtual asset service providers (VASPs), and digital banks.
Institutional risk assessment and individual customer risk profiles must be taken into account in order to meet anti-money laundering (AML) and counter-terrorist financing (CFT) requirements and fulfil monitoring and reporting obligations. In its guidance for a risk-based approach for the banking sector, Financial Action Task Force (FATF) recommends that a bank should have a monitoring system in place that is adequate with respect to its size, its activities and complexity as well as the risks present in the bank.
You don’t have to stand alone against financial crime. Fincrime investigation teams can work together to detect and investigate fraud, and increase the recovery rates by up to 8x with Salv Bridge.
The role of transaction monitoring systems
Transaction monitoring is more about detection and less about prevention: you can’t prevent crime without detecting it. Informed transaction monitoring choices must be a cornerstone of your financial crime compliance programme. With an effective transaction monitoring system in place, you can:
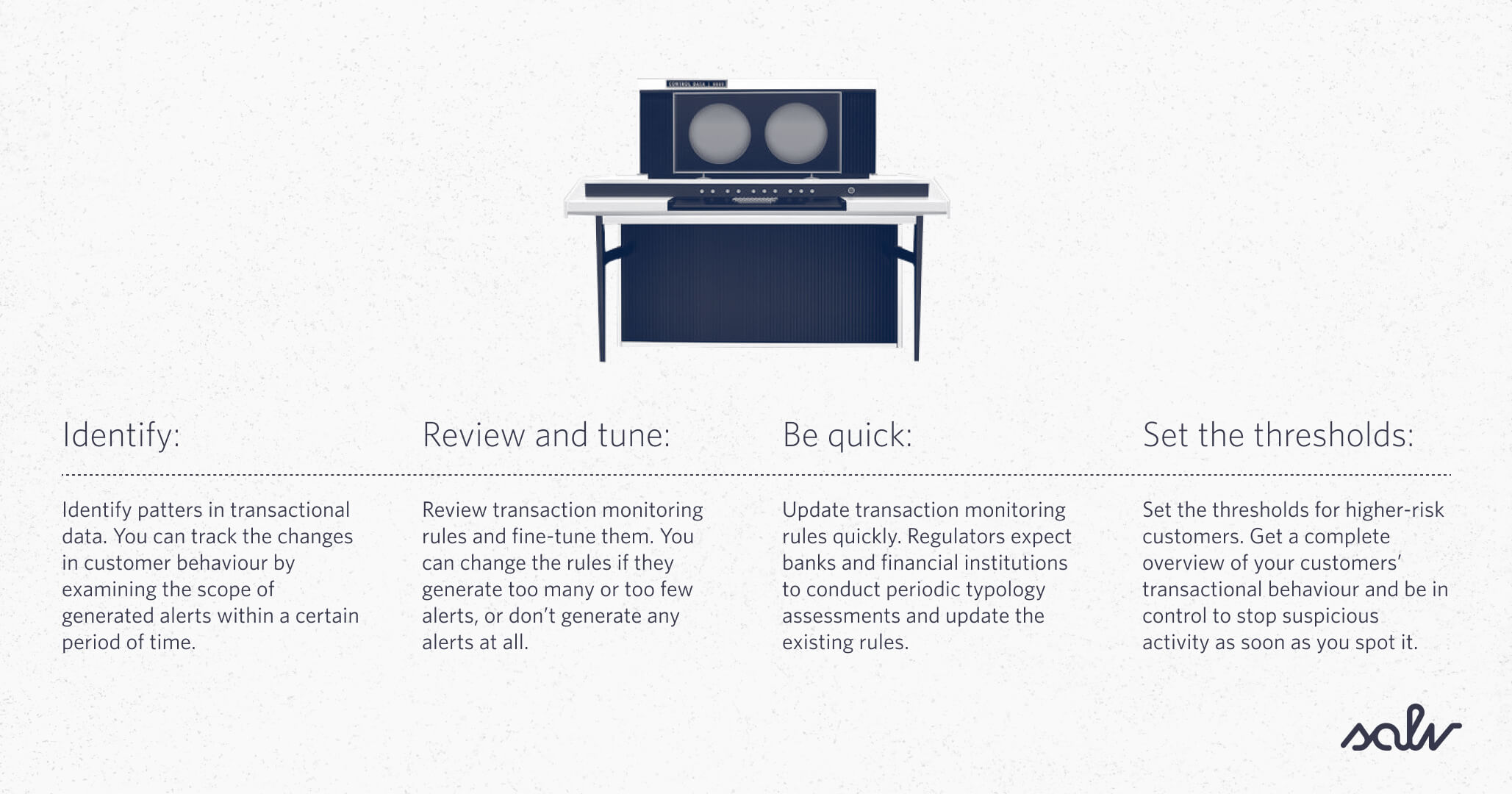
- Identify patterns in transactional data. You can track the changes in customer behaviour by examining the scope of generated alerts within a certain period of time.
- Review transaction monitoring rules and fine-tune them. You can change the rules if they generate too many or too few alerts, or don’t generate any alerts at all.
- Update transaction monitoring rules quickly. Regulators expect banks and financial institutions to conduct periodic typology assessments and update the existing rules.
- Set the thresholds for higher-risk customers. Get a complete overview of your customers’ transactional behaviour and be in control to stop suspicious activity as soon as you spot it.
The key to a successful transaction monitoring system is to constantly monitor, keep track and respond to the threats your organisation and your customers face. You must be aware of the industry-specific risks, identify the weak points in your systems and processes, including your product’s potential vulnerabilities – in order to overcome them. This will provide you with valuable information and insights, and guide you to create effective and efficient transaction monitoring rules to capture all possible risks and threats and stay on top of your game.
What is a transaction monitoring process?
Despite the unique business factors that guide your choice of transaction monitoring process, regulators worldwide prioritise enhanced due diligence for high-risk customers. In transaction monitoring, a risk-based approach means tailoring the process to the customer’s individual risk profile.
FATF has been a strong advocate of a risk-based approach, advising financial institutions to adjust their transaction monitoring processes in line with organisations’ risk assessment and individual customer risk profiles. Under this approach, monitoring should be conducted continuously or be triggered by specific transactions. Salv has further enhanced this approach with a dynamic rules-based engine that allows for creating, changing, and testing flexible transaction monitoring rules, without engineering skills or knowledge, and completely independently.
Transaction monitoring can be executed as a batch process or in real time, where transactions are analysed either as batches by the end of the day or individually as they occur. Although not a regulatory requirement, real-time monitoring offers clear advantages over batch processing, for example, faster and more accurate decision making. The transaction monitoring process should be reviewed regularly to stay aligned with the organisation’s specific business needs and evolving criminal methodologies.
What are transaction monitoring rules?
Many organisations use transaction monitoring to simply tick the boxes. But if you really want to solve money laundering and financial crime, you need to build your own library of transaction monitoring rules. Your rules must cover specific money laundering typologies and target your organisation’s particular risks and vulnerabilities. Whether you are an early-stage startup or an established enterprise, Salv can help you to quickly set up and upgrade your transaction monitoring system.
Transaction monitoring rules focus on capturing suspicious patterns in deposits made to personal and business accounts, as well as money transfers and withdrawals. When set up properly, transaction monitoring rules run through the aggregated transactional data, flagging suspicious transactions for analyst review. With transaction monitoring rules, you can do so much more than just tick the boxes.
What can you do with transaction monitoring rules?
Extensive transaction monitoring rules that encompass a range of complex scenarios can work wonders to bring down the number of false positives, detect patterns of crime, and reduce the workload for your compliance team. Transaction monitoring rules act as a safety net giving you the confidence to stand your ground and fight crime more effectively: you can track irregularities in your customers’ behaviour, as well as their customers’ and counterparties’ transactional history. With Salv, you can create custom rules from scratch with zero engineering effort.
We provide a comprehensive data overview that enables you to understand the relationships between counterparties. This approach forms the core of counterparty monitoring at Salv – read more about how we make that happen.
Unlike artificial intelligence (AI) and machine learning (ML), transaction monitoring rules are explainable and predictable; they easy to understand and implement, as well as to control in terms of input. By incorporating both risk-based and rules-based transaction monitoring, you can control the output by introducing new features to better explain the data. You can communicate transaction monitoring rules in simple terms to legal professionals, external auditors and regulators.
With transaction monitoring rules that accurately capture your organisation’s known and potential risks, you can:
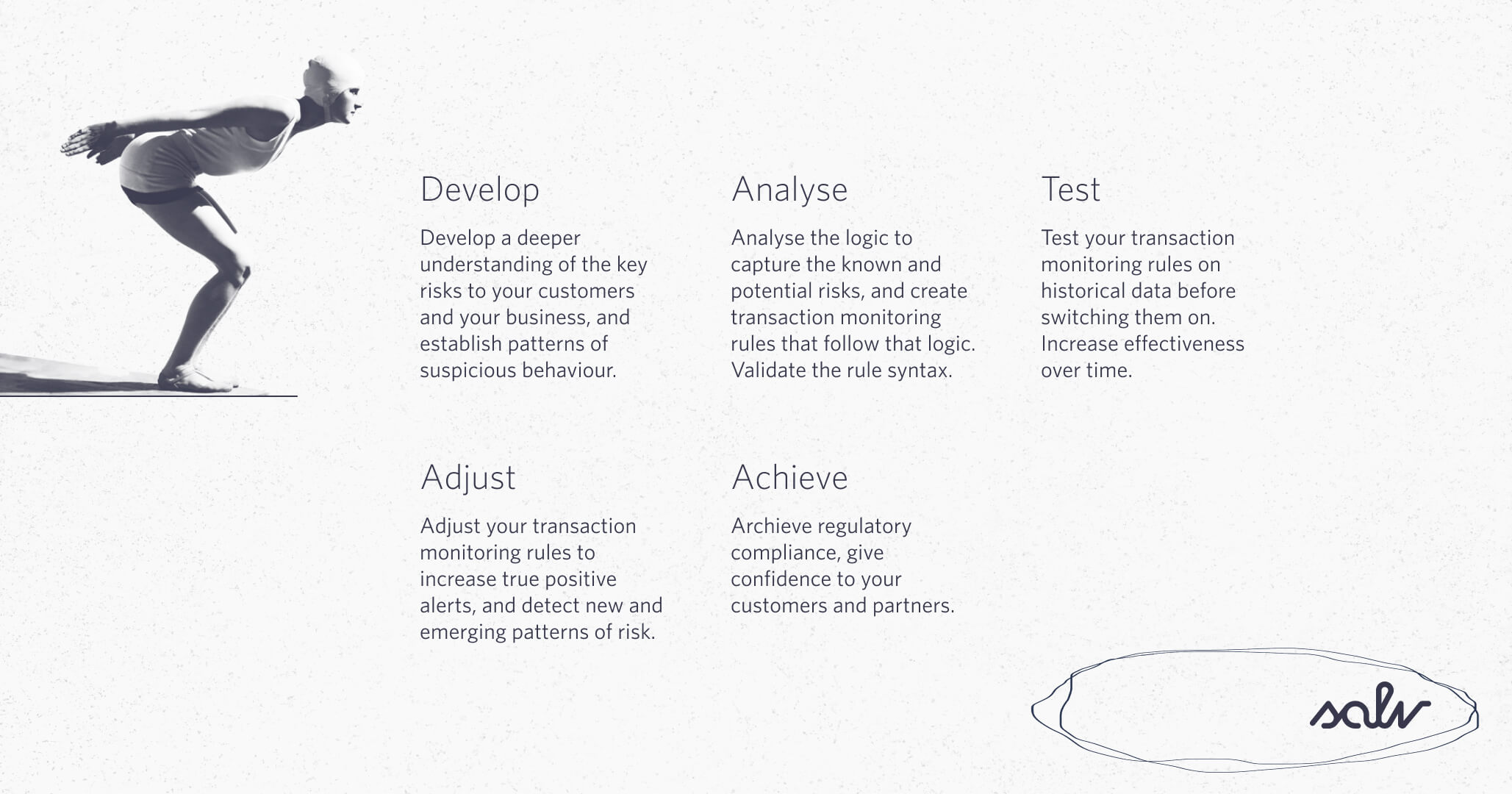
- Develop a deeper understanding of the key risks facing your customers and your business, and establish patterns of suspicious behaviour tailored to their specific needs.
- Analyse the logic to capture the known and potential risks, and create transaction monitoring rules that follow that logic. Validate the rule syntax.
- Test your transaction monitoring rules on historical data before switching them on. Increase effectiveness over time.
- Adjust your transaction monitoring rules to increase true positive alerts, and detect new and emerging patterns of risk.
- Achieve regulatory compliance, give confidence to your customers and partners.
How do transaction monitoring rules work?
What types of data we process
Salv processes customer data, both transactional data and non-transactional data, or metadata. You can create and test better transaction monitoring rules using risk and screening results, internal compliance knowledge, exclusion lists or multiple country lists, as well as know-your-customer (KYC) and know-your-business (KYB) data. As long as you have a coherent and consistent dataset that provides a solid base for the analysis, it’s safe to say, you are set up to succeed.
What types of rules you can create
With Salv, you can create rules for real-time, post-event and periodic transaction monitoring checks. Real-time transaction monitoring rules empower you to stop fraudulent transactions when they occur by giving you a real-time API response. If you don’t need to suspend a payment, and there is no other business logic triggered, it’s often best to use post-event transaction monitoring rules. They don’t require a separate monitoring check API call: all the calculations are done after the data is uploaded to the Salv platform. Instead of being triggered by new data uploads, periodic — sometimes called interval — scenarios run continuously after the time interval you define.
With Salv’s transaction monitoring rules you can monitor high-value transactions, payment frequency, velocity, counterparty count, dormancy, and more. In terms of payment methods, within Salv Platform, you can monitor payments processed through Swift, SEPA Transfers & Instant, Faster Payments, BACS, Direct Debits without any limitations. You can monitor your customers, including natural persons, legal entities, merchants, the end customers of your customers, and counterparties. You can do so much more – with one convenient solution.
How transaction monitoring rules work
Whenever you see something strange or suspicious, you can write a rule to capture and investigate it, detect similar patterns in the future, and make sure that the same thing doesn’t happen again. The process is fairly simple: you collect the input, create a rule, validate the syntax, test the rule on historical data, and implement it into the production environment. At Salv, we currently support two languages: SQL and JMESPath, intuitive and powerful query languages that are easy to grasp and start using from day one.
Salv utilises fuzzy matching for name matching in transaction monitoring to identify fraud in third-party payments. Incorporating transaction monitoring alerts, together with the decisions, into scenarios increases the accuracy and precision of your transaction monitoring rules. This, in turn, results in a reduced and more streamlined workload.
The more transaction monitoring rules you have, the greater your chances of detecting the patterns that may have previously escaped your attention. Salv’s customers don’t have to create everything from scratch (although that is also an option): we have a growing library of transaction monitoring rules, with 100+ rules being used daily by dozens of our customers. At Salv, we regularly generate more combinations and update our library with new granular rules. Each rule is a template that can be easily adjusted for your organisation’s risk factors.
With Salv, you can set up certain thresholds depending on the risk levels of your customers.
Salv’s risk scoring tool allows you to pinpoint higher-risk customers and incrementally increase efficiency over time.
Examples of transaction monitoring rules
Transaction monitoring rules follow a straightforward logic that can be adjusted based on what is relevant to your organisation at any specific point in time. You can set these rules to flag transactions that exceed certain thresholds or originate from specific geographic locations. You can flag accounts for fast movement of funds, particularly when the account holder withdraws up to 90% of the balance, as well as any sudden change in customer behaviour. And there is more. Both individual and business accounts can be monitored for what you define as suspicious activity.
When the rule’s conditions are fulfilled, the system generates an alert. A compliance officer will then review the alert to assess the situation and take appropriate action.
Transaction monitoring alerts
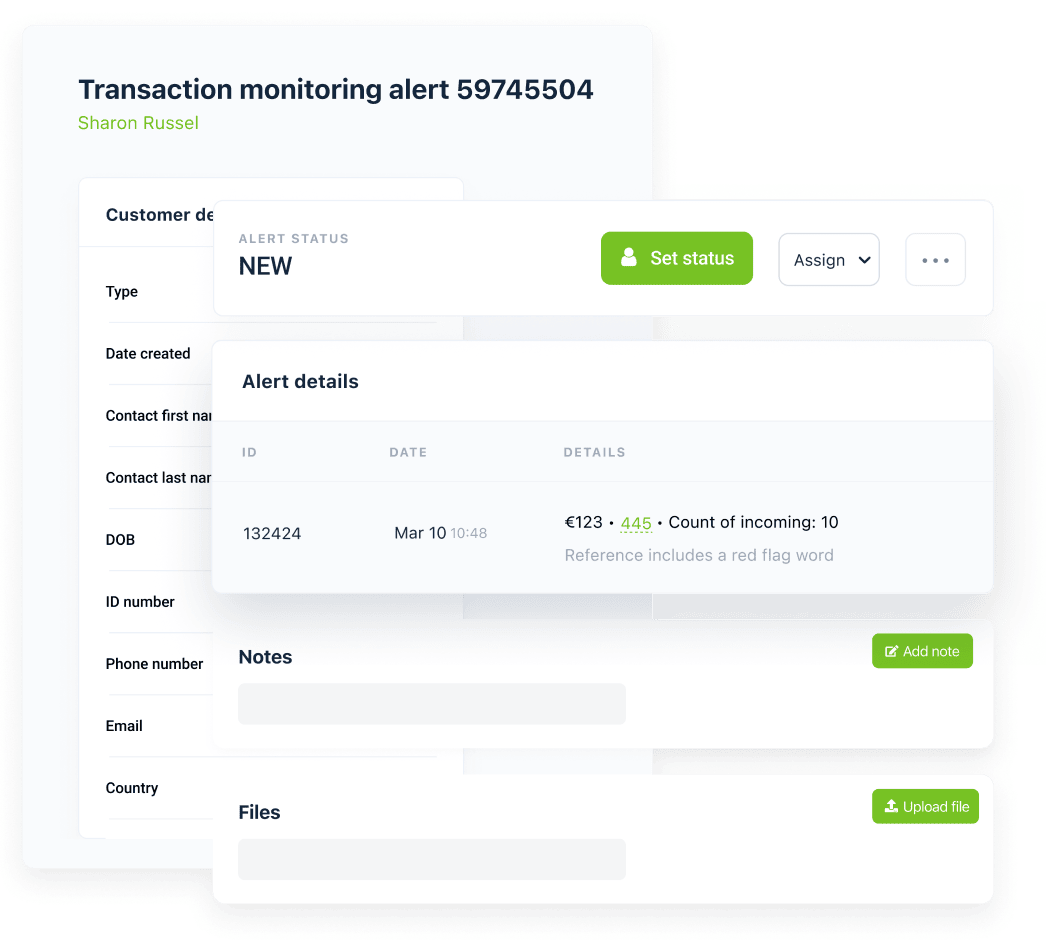
Transaction monitoring allows you to act fast. When you receive an alert, you want to quickly access the specific transaction that triggered it and start an investigation. Salv does that for you by simplifying the handling and managing of transaction monitoring alerts – you can access everything you need in one page.
Salv aggregates person and transaction monitoring parameters, including all alerts that were triggered by the same transaction, along with the reasons. If you have more than one alert for a customer, you can solve them all in one go.
Alerts can be assigned to others, which simplifies the team management process and balances individual workloads. You can add, search, and filter notes. The statuses help you understand how the investigation is progressing, and a new person can easily take over and continue the work started by someone else.
You can filter monitoring alerts using person and transaction attributes, scenarios, and risk levels, including flagging payments going to a specific country. You can easily adjust the filters to match your payment operations and payment processing deadlines, and manage your compliance team by distributing the monitoring alerts across the team.
Once the alert is reviewed, you can update the customer’s status, including suspension and termination, or snoozing alerts for a customer. It’s safe to say that handling transaction monitoring alerts in Salv effectively minimises customer impact.
Challenges in transaction monitoring process
Financial criminals are fast: they have the latest technology, unlimited freedom and resources to stay one step ahead of law enforcement efforts. Compliance teams need more time to investigate and prevent money laundering, more often than not, they are understaffed. But that’s not all there is to it.
When it comes to inefficient transaction monitoring processes, organisations face even greater challenges, in part due to:
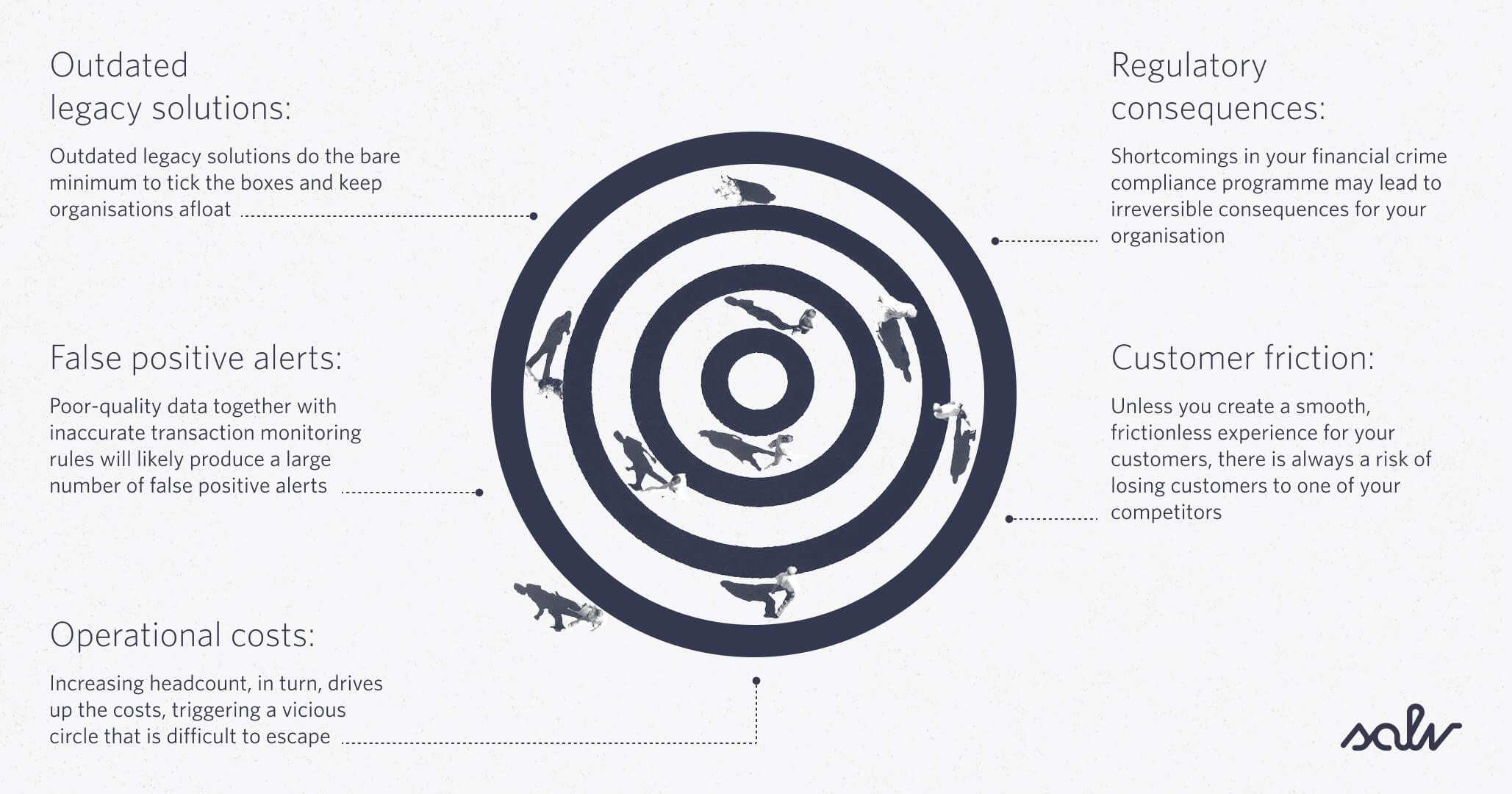
Outdated legacy solutions
At some point in the past, existing legacy solutions were ahead of their time. Now they are more like dinosaurs who somehow survived the asteroid crash. Outdated legacy solutions do the bare minimum to tick the boxes and keep organisations afloat. Placing blind trust in an antiquated legacy system can put you in danger of inaccurate regulatory reporting and lead to constant, costly maintenance.
False positive alerts
It’s not a secret that poor-quality data, together with inaccurate transaction monitoring rules will likely produce a large number of false positive alerts. Organisations who go down that path are faced with two options: hire large teams to keep up with the growing workload, or choose transaction monitoring software to minimise operational risk and keep compliance costs in check. The rules should be reviewed periodically, preferably on a monthly basis, to balance growing alert workload and avoid alert fatigue.
Rising operational costs
Faced with a growing number of false positives, you need someone to resolve the alerts and clear the alert backlog. Increasing headcount, in turn, drives up the costs, triggering a vicious circle that is difficult to escape. It’s not always easy to understand and calculate your compliance costs. A while ago, we wrote a blog on how to measure your AML compliance costs.
Applying human hours doesn’t solve the problem; rather data analysis and automation do.
Customer friction
Customer friction is dangerous. Unless you create a smooth, frictionless experience for your customers, there is always a risk of losing them to one of your competitors. You don’t want your transactions to be routinely suspended for money laundering checks, and neither do your customers. Focusing on your customers’ safety and convenience is essential to increasing customer satisfaction, trust and loyalty.
In this time and age, regulators want more than compliance. They want you to fight crime. But how can you measure your crime-fighting effectiveness?
With Salv, you can create, test, and change your own rules, even with limited technical skills and knowledge. This gives you more control over your transaction monitoring system and the decisions you make. Implementing smart rules to detect suspicious behaviour more quickly will help you scale your operations while intelligently balancing compliance and business needs.
Use our transaction monitoring rules to review your entire compliance framework, before launching a new product, and to quickly adjust thresholds to the transaction appetites of your growing customer base.
We don’t give you a tick-box solution. We want you to be on top of your game to beat financial crime and move the industry forward. At Salv, we created a complete toolkit for your organisation, to use your compliance knowledge and experience for the benefit of your customers and help you to become better at what you do.
With Salv, you can use a custom logic to generate alerts and create transaction monitoring rules in a very flexible way, with no limitations, no right or wrong, and a freedom to build and explore. You don’t need a deep technical understanding or engineering experience: test and adjust the rules as you like. We’ve got you covered.
- What is transaction monitoring?
- What is a transaction monitoring process?
- What are transaction monitoring rules?
- What can you do with transaction monitoring rules?
- How do transaction monitoring rules work?
- Examples of transaction monitoring rules
- Transaction monitoring alerts
- Challenges in transaction monitoring process